Configure G-suite connector
- 09 Nov 2023
- 2 Minutes to read
- Print
- DarkLight
- PDF
Configure G-suite connector
- Updated on 09 Nov 2023
- 2 Minutes to read
- Print
- DarkLight
- PDF
Article summary
Did you find this summary helpful?
Thank you for your feedback
Steps to configure the connector:
- Login to Cross Identity and go to the admin console.
Download the CID Agent file
- Click Advanced > Download.
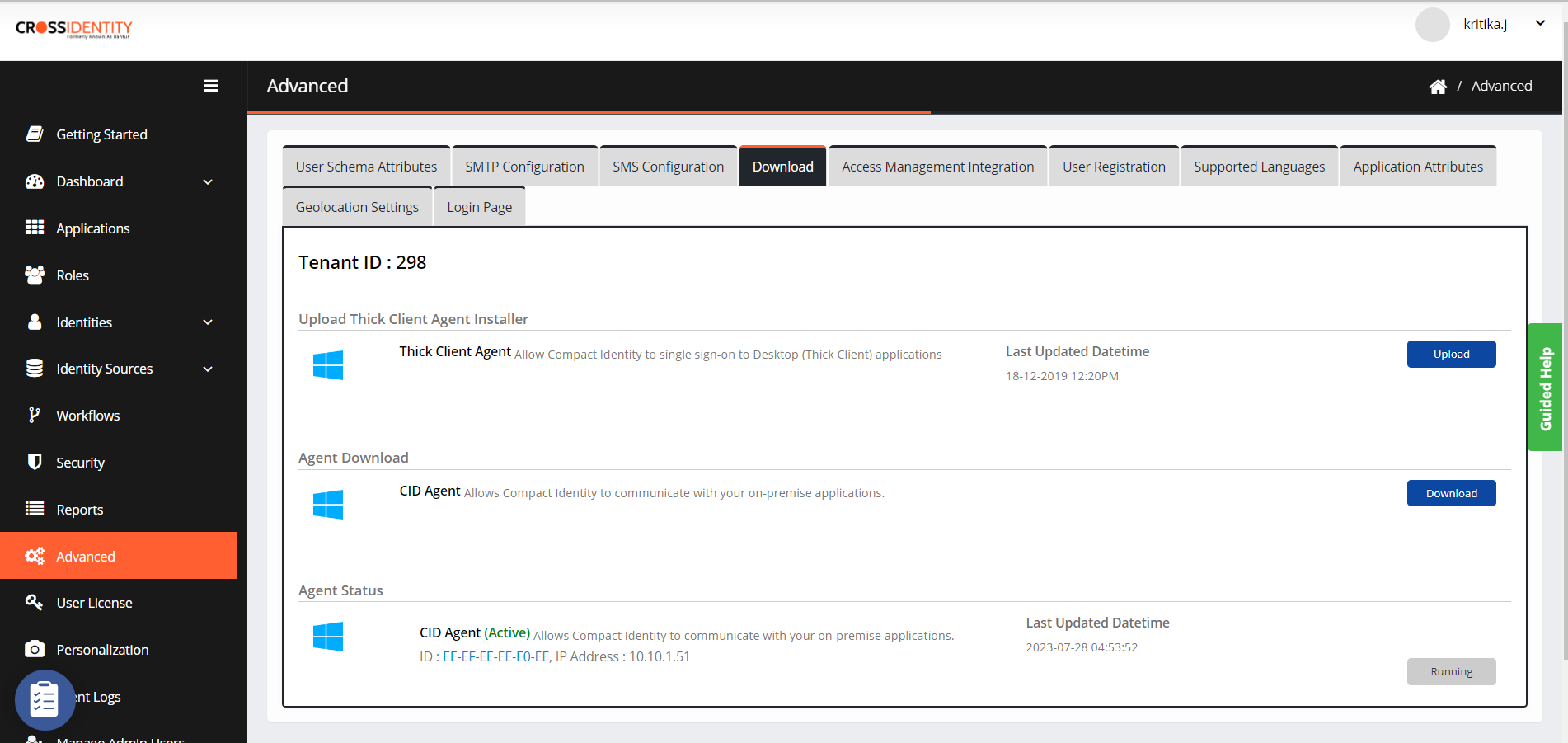
- Click Download from CID Agent as highlighted in the image.
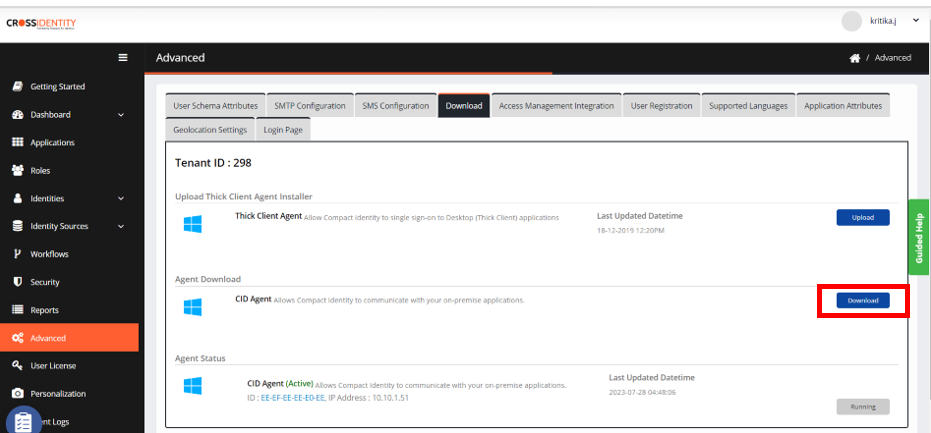
- After downloading the CID Agent, navigate to C:\Program Files\Apache Software Foundation\Tomcat 9.0\webapps\CIDAgent\WEB-INF\classes and verify the parameters.properties file.
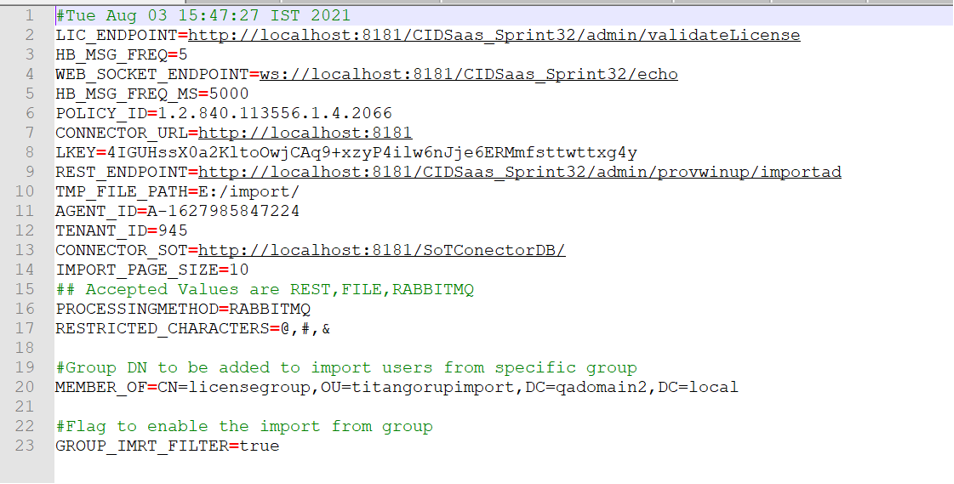
- Make changes for LIC_ENDPOINT, WEB_SOCKET_ENDPOINT, and REST_ENDPOINT as per the tenant URL received for CI.
- Make changes for CONNECTOR_URL, and CONNECTOR_SOT as per the Apache tomcat port number.
To utilize the RabbitMQ feature, mention PROCESSING METHOD as RABBITMQ. If not, mention REST. - After making the necessary changes save the file.
Onboard G-suite application in CI
- To add a required application from the global app store, go to the Applications > click the ‘+’ symbol to add an application.
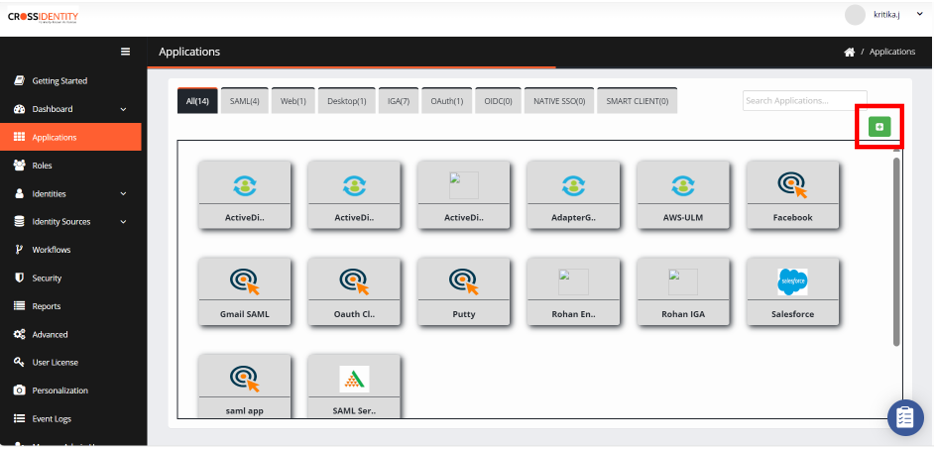
- In the AppStore pane, search the ServiceNow application.

- Once it is displayed, click on it and it will take you to the application configuration window.
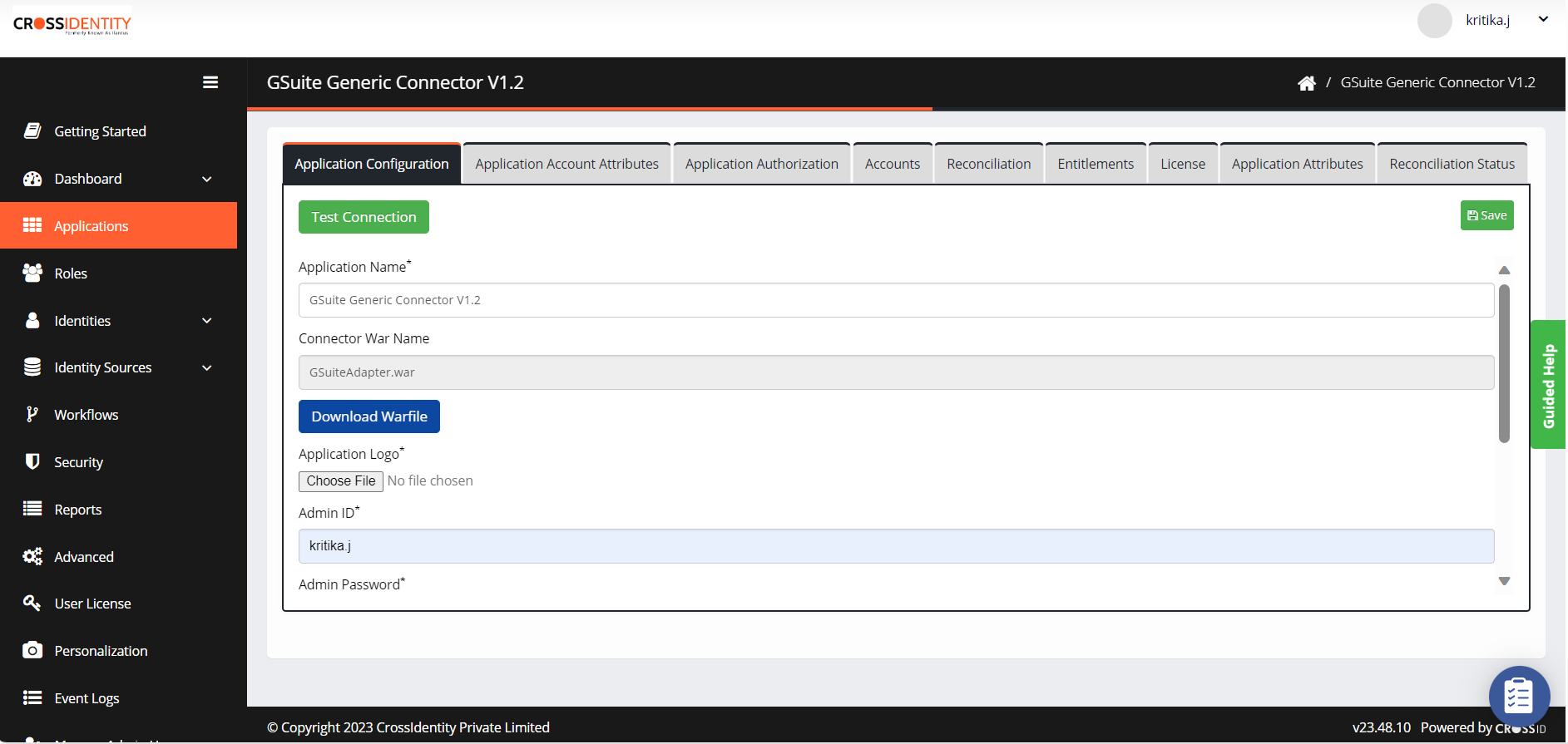
- Fill out the required details in the Application Configuration tab.
- Application Name: Provide a name. Example: Gsuite.
- Connector War name: This is an uneditable text field.
- Application logo: Choose a logo for the application.
- Click Save.
- Check for Gsuite war file in C:\Program Files\Apache Software Foundation\Tomcat 9.0\webapps.
 Note:The folder path may vary from client to client.
Note:The folder path may vary from client to client. - If the Gsuite.war file doesn’t exist in the above location, download the war file from CI. (Go to Applications menu > Application Configuration tab > click Download WarFile)
- Once the war file is downloaded, keep it in C:\Program Files\Apache Software Foundation\Tomcat 9.0\webapps and restart the agent.
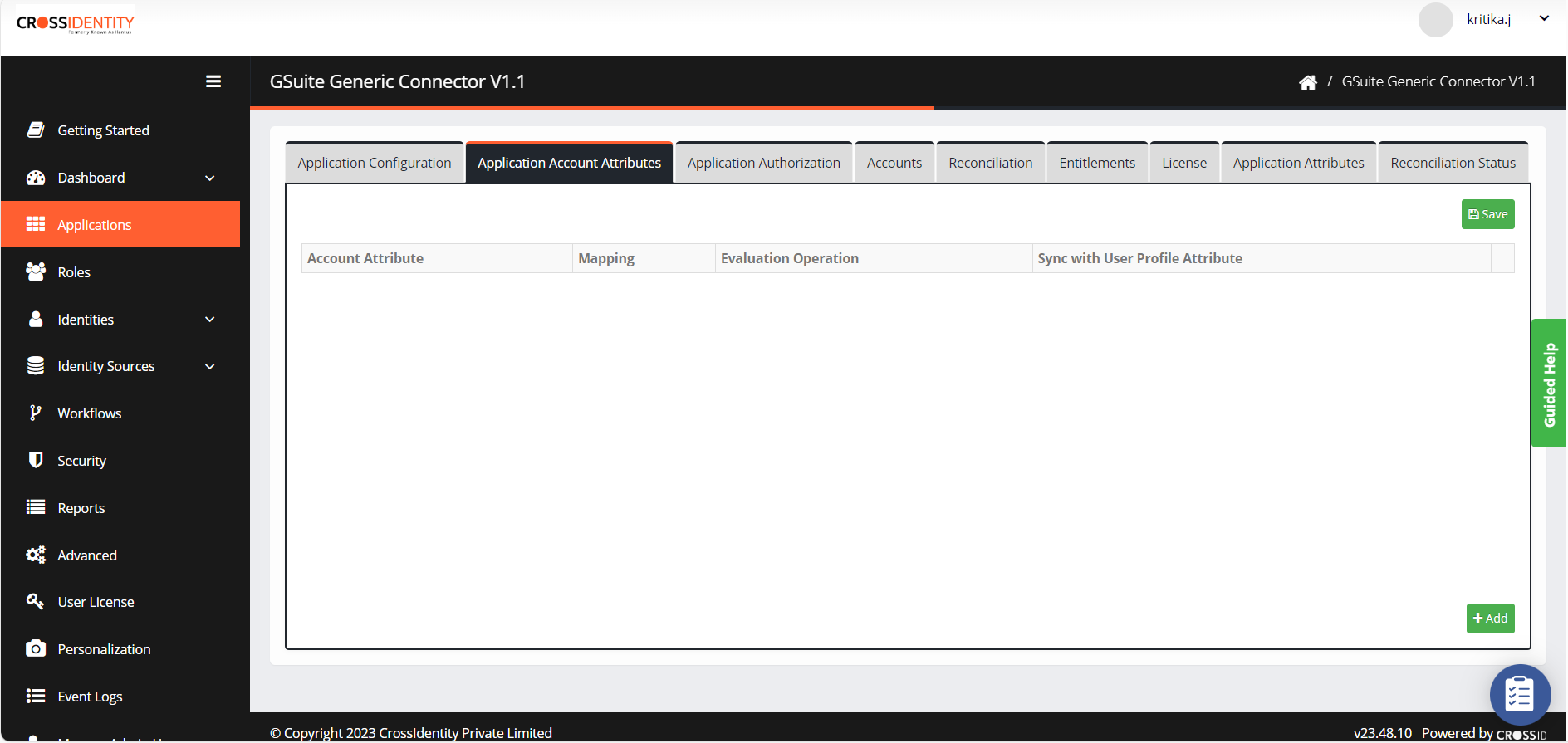
Application Account Attributes
- Go to Application Account Attributes and click +Add.
- Select the necessary attributes by checking the appropriate boxes and then click ADD.
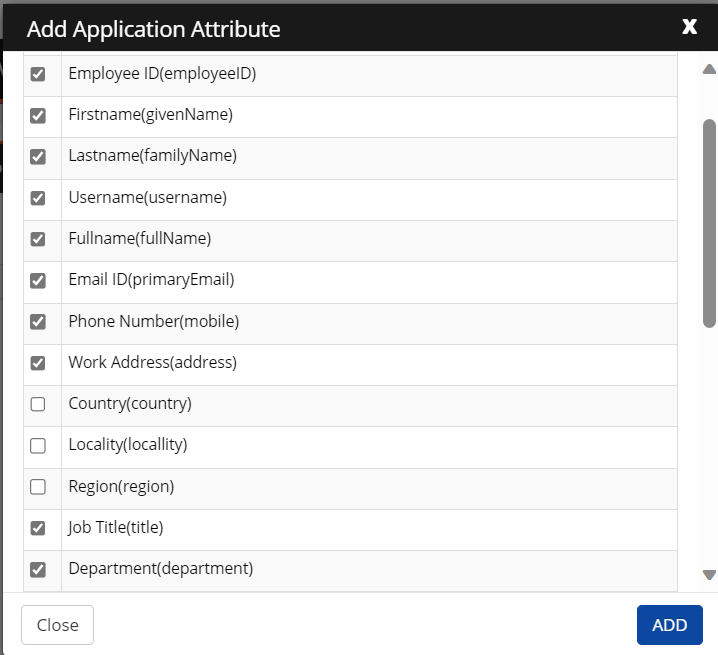
- On the next screen, you can see the added application account attributes and map the attributes as per requirement.
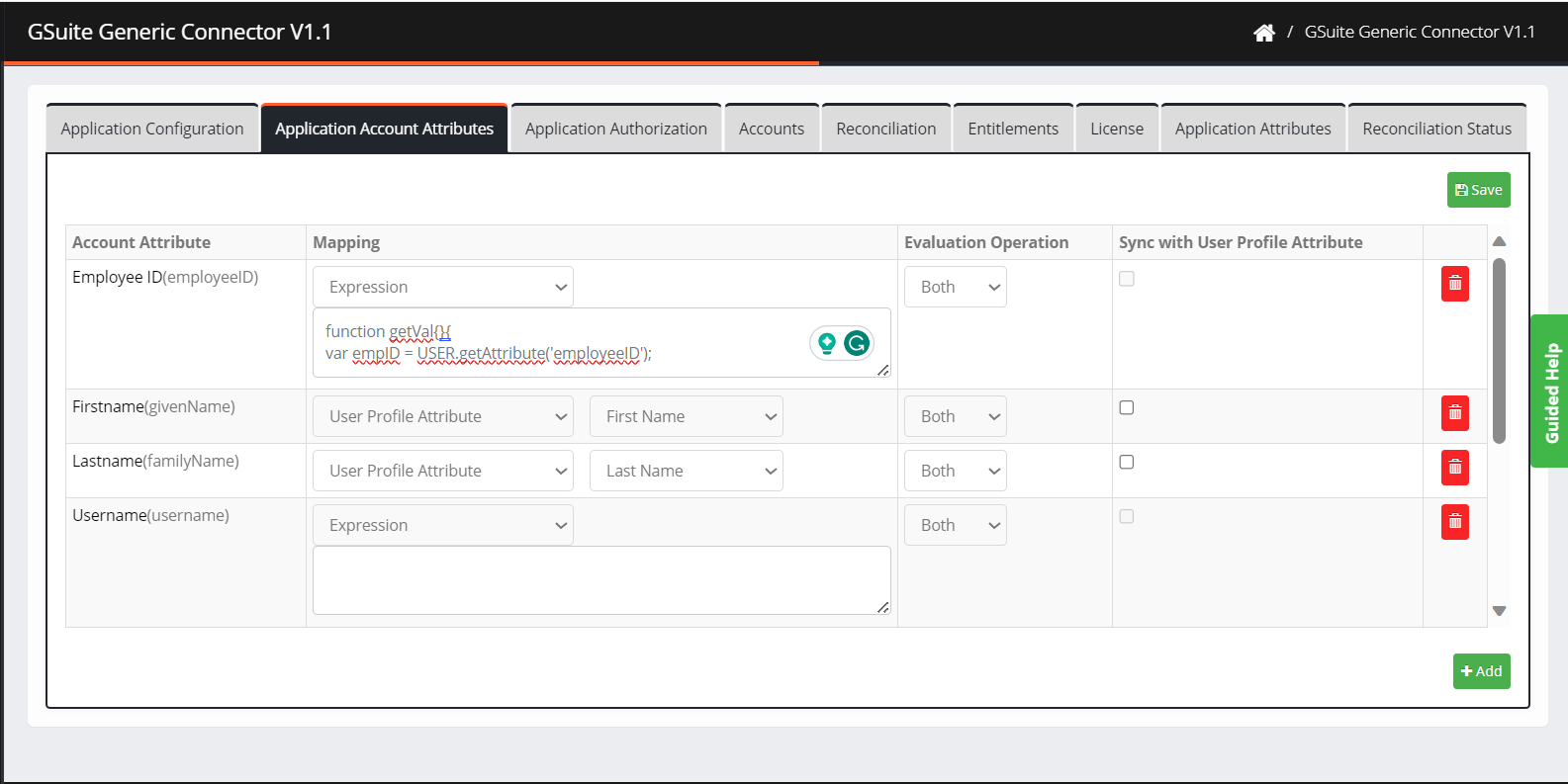
- Select the Mapping method from the drop-down.
- User Profile Attribute: When you choose this option, you need to define a user attribute that matches with Active Directory.
- Assigning Group to the user based on expression calculation from UI:
Groups can be assigned as per the business logic and the same is achieved by defining expressions in CI as shown below.
- Evaluation Operation: Select Create, Modify, and Both from the drop-down. It applies to a user account with the selected account attributes.
- Sync with User Profile Attribute: Check the box to sync account attributes from the target application to Cross Identity.
Add Roles in Cross Identity
- Navigate to Roles from the menu.
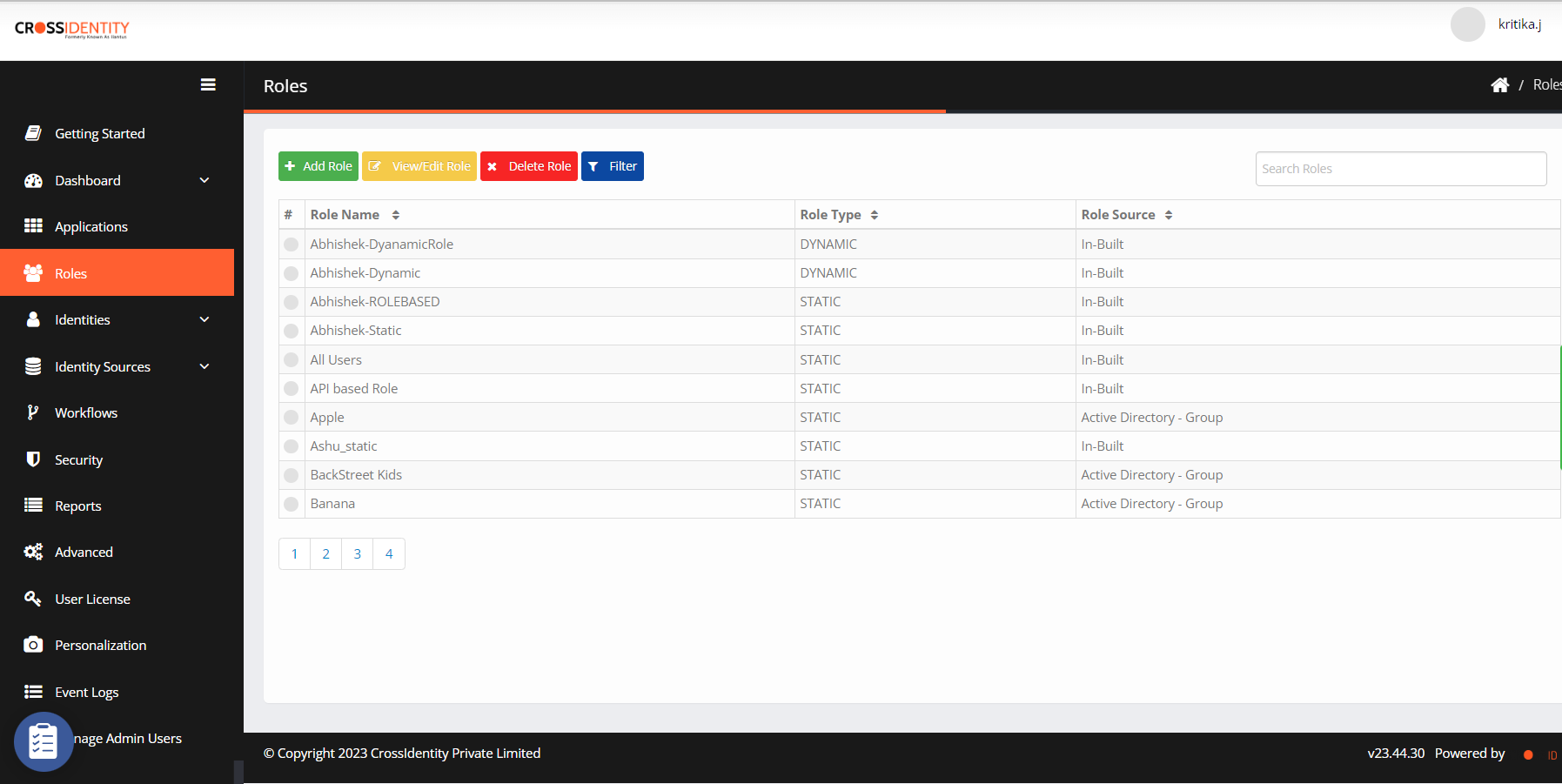
- Click Add Role. The Add Role screen appears.
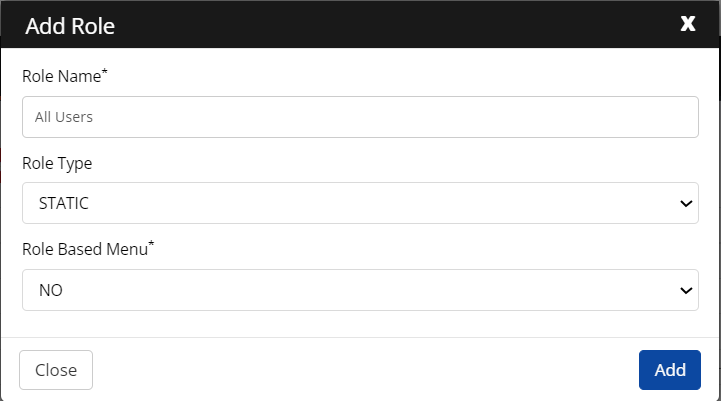
- Click ADD.
Application Authorization
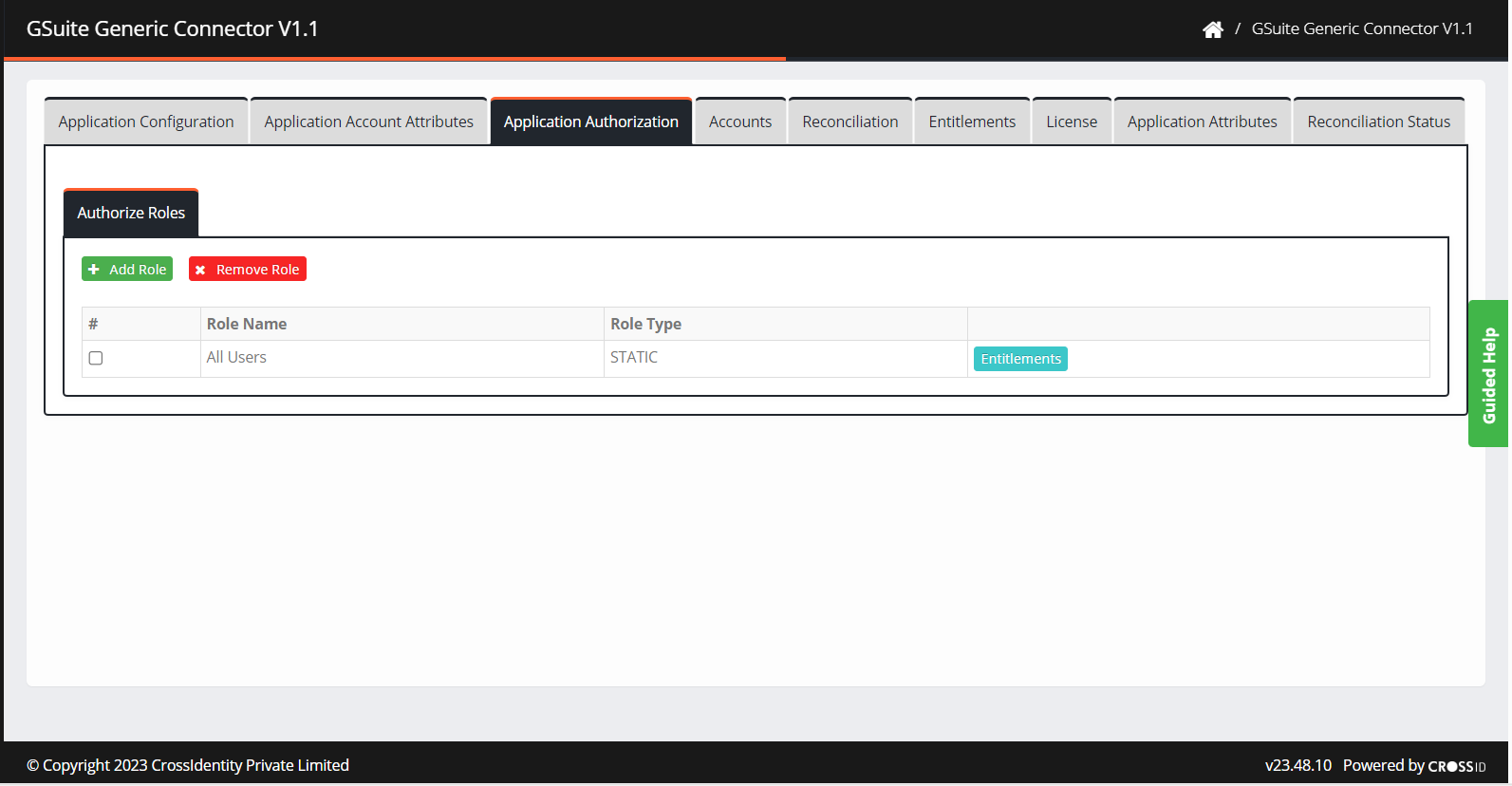
- Navigate to Application Authorization. The application authorization screen is displayed.
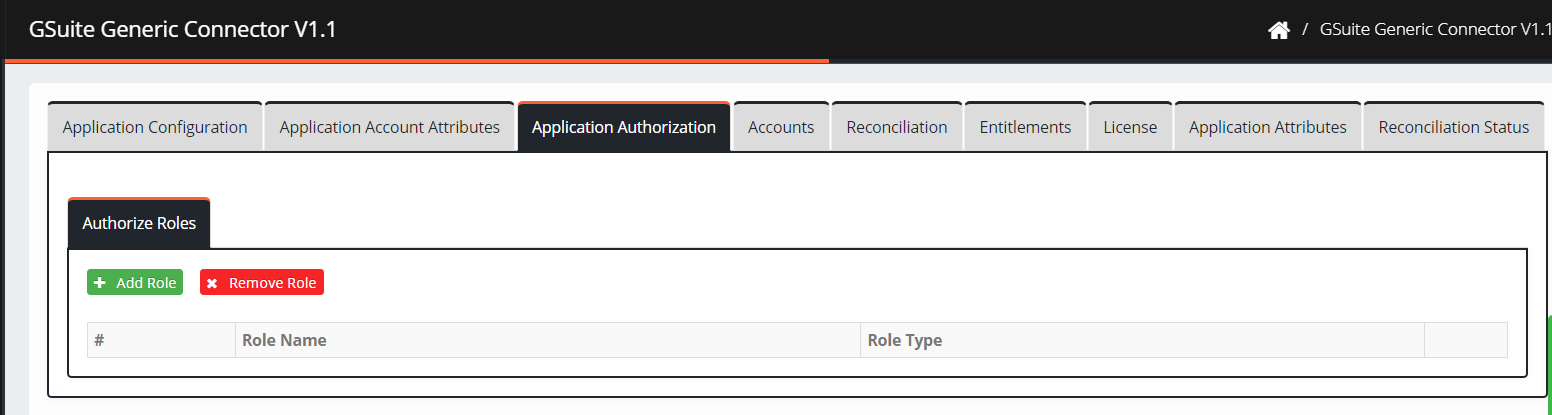
- Click Add Role and search for the role added in CI.
- Select the appropriate role and click ADD.
Accounts
- Navigate to Accounts.
- Select a unique attribute to link to identity and configure it as a display attribute.
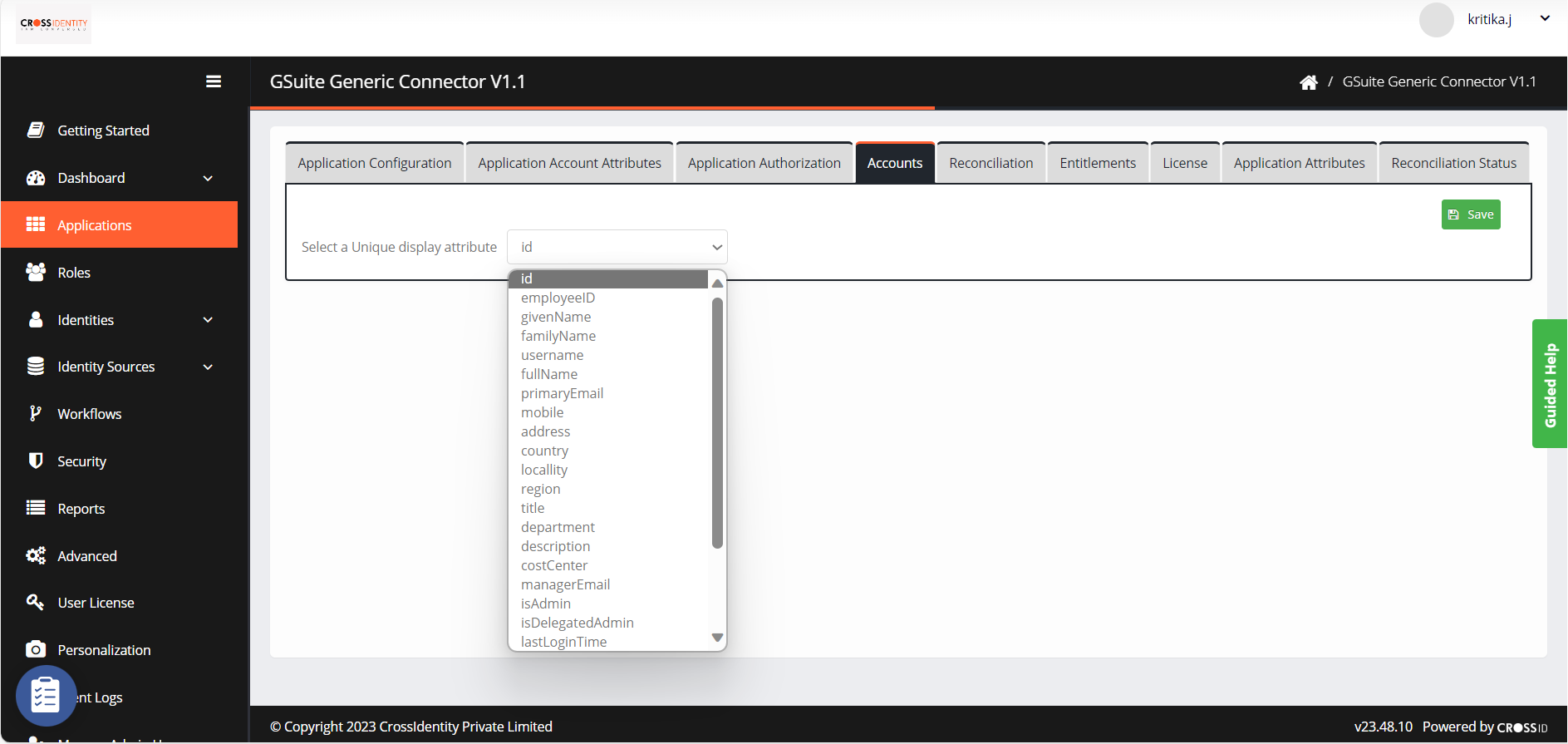
- Click Save.
Entitlements
- Navigate to Entitlements.
- Click Entitlement Definition > Add Entitlement Definition.
- Set Entitlement Definition:
Sr. No. Entitlement Name Entitlement Key Entitlement Value 1. Group (could be any user-friendly name) group group 2 OU(could be any user-friendly name) ou organizationalUnit 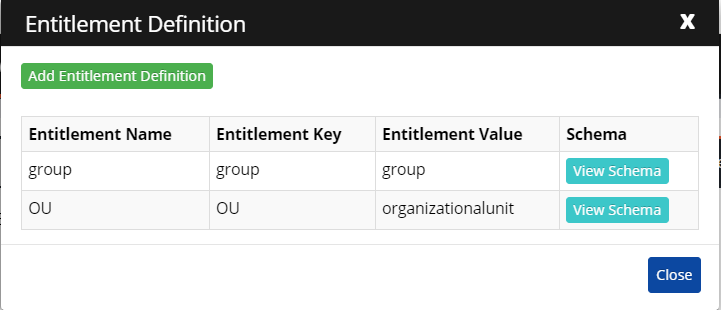
- The entitlement key and value are checked in a connector to fetch group details and OU details respectively. As per the schema defined, the group names and its members are fetched and will be displayed in the entitlement tab.
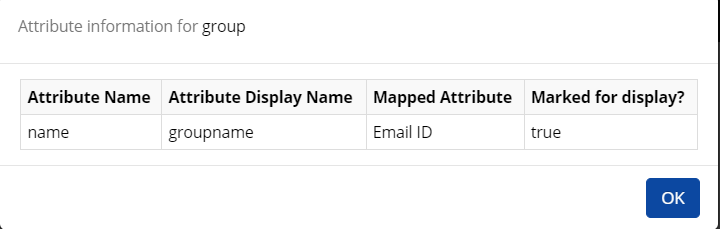
- Set schema details: In Connector, Attribute Name fields are used to fetch group names and members of that group from respective API responses. Attribute Display name is a user-defined display name. The mapped Attribute is mapped to the Display Name (as we are considering the Display Name as a unique key attribute) which represents the Group name, and the chosen will be displayed in the CI UI entitlement section.
Sr. No.
Attribute name
Attribute Display Name
Mapped Attribute
Marked Display?
1
name
groupName
emailID
Yes
2
member
member
emailID
No
 Reconciliation
Reconciliation
The Recon rule is a must to link the CI identity and its respective account from the Target application using a unique link attribute (like email, employee ID, sAMAccount name, etc.). Multiple attributes can be considered by choosing the priority.
- Navigate to Reconciliation.
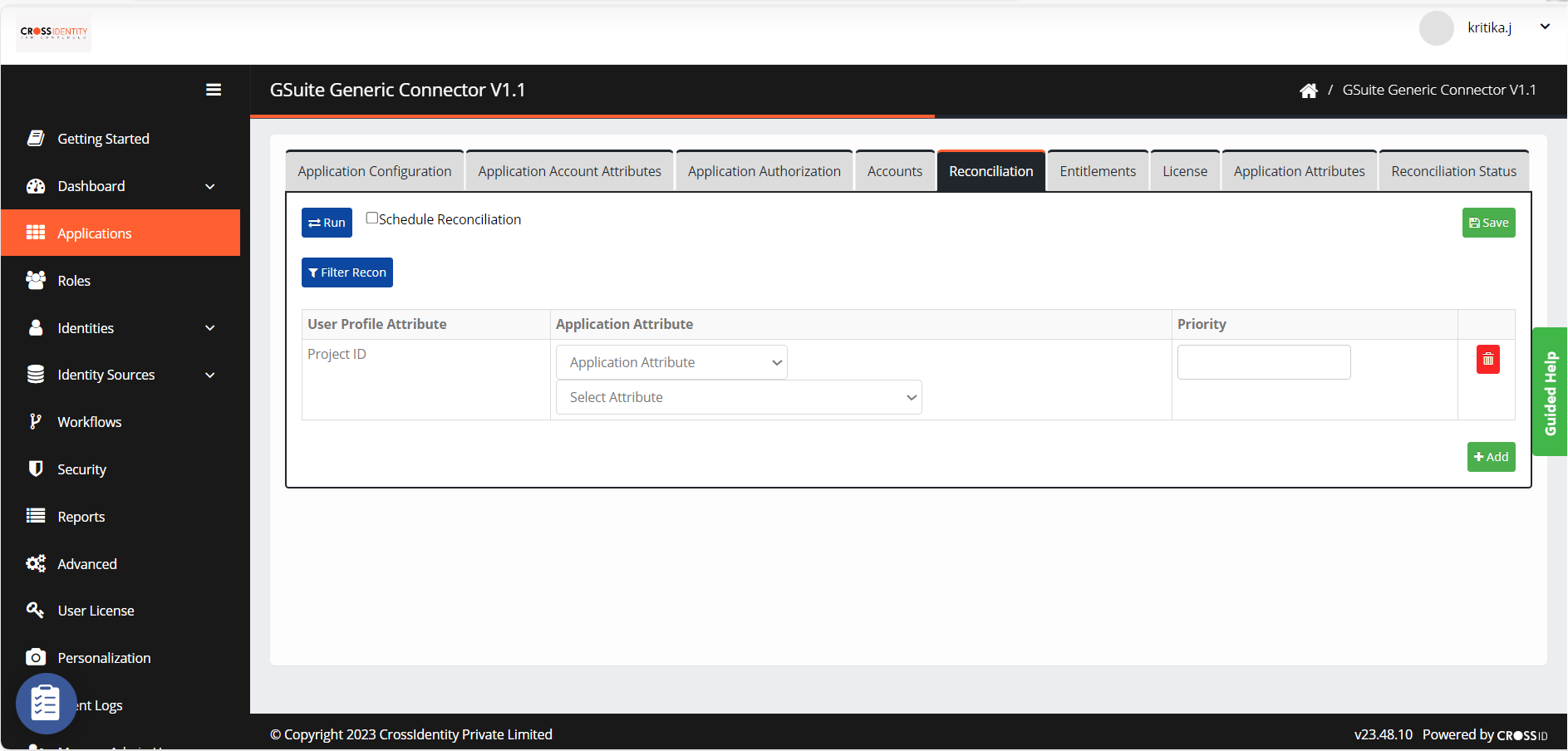
- Click Run to initiate the recon.
Was this article helpful?
.png)




















 Reconciliation
Reconciliation
.png)